Cognitive Radio Cognitive Network Simulator (NS3 based)
Table of Contents:
1
Introduction to CRCN
1.1
Background
of Cognitive Radio
1.2
Motivation
1.3
Why
Based on NS3?
1.4
CRCN
Simulator Overview
2
Simulator Overview
2.1
System Requirements
2.2
Functionality Overview
2.3 Design Overview
2.3.1 Design of CR MAC/PHY
2.3.2 Design of Spectrum Database
2.3.3 Design of Attack Model and its Interface
2.3.4 Design of Spectrum Coordinator and its Interface (under construction)
2.3.5 Example Script for Simulation Configuration
3
CRCN
User Guide (under
construction)
3.1
Software and Installation
3.2 Examplary Demonstrations
3.3
GUI User Guide
4
Miscellaneous
(under
construction)
4.1
References
4.2
FAQ
4.3
Cognitive Radio Research Group
1. Introduction to CRCN
1.1
Background
of Cognitive Radio
Cognitive
Radio Cognitive Network (CRCN) is a promising technology that has been studied
in the research area for a long period. With CRCN, the problem of spectrum
scarcity and spectrum underutilization might be effectively solved [1]. This is
attributed to the Dynamic Spectrum Access/Allocation (DSA) mechanism [2] of
CRCN, which allows the CRCN subscribers to opportunistically occupy the
spectrum resources that assigned by the FCC to the licensed networks (primary
users) avoiding interfering to them. The coexistence of CRCN with primary users
necessitates the CRCN nodes to be capable of being aware of their surrounding
environments (e.g., the availability of a specified channel band), which is
called spectrum sensing [3]. The spectrum sensing is facilitated periodically (e.g.,
specified in IEEE802.22 standard [4]). Once the channel bands are detected to
be unoccupied by the primary user, the CRCN may request to access into these
channel bands. Otherwise, the CRCN immediately vacant the channel bands that
occupied by the primary user and move to the other available bands. The CRCN
coexists with not only the primary users, but also other CRCNs since multiple
CRCNs may work simultaneously over the same available spectrum bands [5]. This results
in even more complicated design of CRCNs since both interference to the primary
users and CRCN’s network performance should be optimized simultaneously [6].
Security
is another significant topic considered in the design of CRCNs [7, 8]. Due to
the cognitive features of CRCN (e.g. spectrum sensing and coexistence with
primary users etc.), specific attacks for the CRCNs have been proposed in the
literature, such as Primary User Emulation Attack (PUEA) [9, 10], Spectrum
Sensing Data Falsification (SSDF) [11, 12], Jamming on Common Control Channel
[13, 14] and so on. Without the effective defense approaches to these attacks, the
CRCN performance will degrade severely and it may lead to the low spectrum
utilization efficiency. Furthermore, the primary network might be interfered by
the CRCN due to the fake spectrum sensing reports caused by the adversaries. A
number of approaches have been proposed to defending against those attacks. However,
considering the deployment of CRCN in reality, novel security challenges will
be found which necessitates more effective and efficient solutions.
1.2
Motivation
of upgrading the CRCN simulator
As
cognitive radio research is emerging, more and more researchers are looking
forward to a simulator that is suitable for cognitive radio. However, there is
no existing simulator that is suitable for the demand of cognitive radio
simulations. Many researchers
implemented their algorithms for cognitive radios on existing network simulator
such as NS-2 [15], OPNET [16], QUALNET [17]. However, since these simulators
are created for the ordinary wireless network, researchers cannot easily
implement their cognitive radio algorithms over those simulators. Hence, there
is a demand to extend existing simulators to support cognitive radio
simulators.
We
have developed a CRCN simulator with NS-2, and this version has been widely
utilized in the academia field. We are attempting to upgrade our CRCN simulator
with NS-3 [18] according to the following reasons:
1)
Security
is one of the important issues in the research of CRCN, we will provide the
attack model interface in this updated version for users to evaluate the
effects of their proposed attack models. Some of existing attack models will be
given as example to show how to embed the attacks into the CRCN simulator.
2)
The
coexistence issue of CRCN has been drawing more attention of researchers. This
propels us to provide the coexisting module interface to the users to evaluate
their coexisting mechanism.
3)
Recently,
the development of CRCN has been paid more attention in the industrial field
wherein a number of realistic constraints are considered. In order to make the
network simulation more realistic, we attempt to develop the CRCN simulator
with a tool which can be easily integrated into the hardware which can be
considered as a network node. Eventually, a network testbed will be built with the
network nodes implemented by the hardware integrated with our CRCN simulator.
1.3 Why
based on NS-3
NS-3
[18] inherits many advantages from NS-2, for example: 1) NS-3 is open source
software, thus any contributions to the NS-3 are accessible by the people
around the world; 2) NS-3 provides many radio models such as 802.11, 802.16,
802.15.3, 802.15.4. Users can make use of these radio models for cognitive
radio network simulations; and 3) NS-3 has incorporated with different topology
and traffic generators, which enable users to create different simulation
scenarios etc.
Compared
with NS-2, NS-3 has following extra advantages [19, 20]:
1)
A
simulation script can be written as a C++ program, which is not possible in
NS2.
2)
With
modern hardware capabilities, compilation time was not an issue like for NS2, NS3
can be developed with C++ entirely.
3)
Ns-3
enables the testbed-based researcher to experiment with novel protocol stacks
and emit/consume network packets over real device drivers or VLANs. The
internal representation of packets is network-byte order to facilitate
serialization.
4)
NS3
performs better than NS2 in terms of memory management.
5)
The
aggregation system prevents unnecessary parameters from being stored, and
packets don't contain unused reserved header space.
1.4 CRCN Simulator Overview
This
cognitive radio cognitive network (CRCN) simulator is a software based network
simulator for network-level simulations. It is based on open-source NS-3
(network simulator 3). CRCN simulator will be able to support performance
evaluations for the proposed dynamic spectrum resource allocation, power
control algorithms, coexistence mechanisms and the adaptive Cognitive Radio
(CR) networking protocols such as the CR MAC protocols. The effects of attack
models can also be evaluated using this CRCN simulator. This simulator uses NS-3
to generate realistic traffic and topology patterns. For each node in this
simulator, a reconfigurable multi-radio multi-channel PHY layer is available by
customizing the spectrum parameters such as transmission power etc.
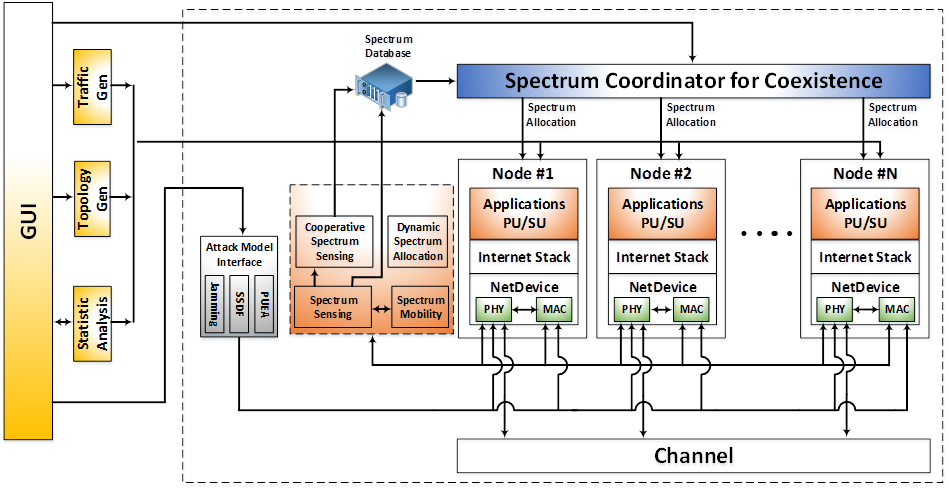
Figure 1. Architecture of CRCN Simulator